




Distributed Denial of Service (DDoS) attacks are among the most disruptive cyber threats faced by organizations today. Unlike attacks that steal data quietly, DDoS attacks are loud, aggressive, and designed to bring digital services to a complete halt. As businesses become more dependent on online platforms, understanding DDoS attacks is no longer optional—it is essential for survival in the digital ecosystem.
This article explains what DDoS attacks are, how they operate, why they are dangerous, and how organizations can prepare for them.
A DDoS attack is an attempt to make an online service unavailable by overwhelming it with excessive traffic. Instead of a single source sending requests, a DDoS attack uses thousands or even millions of systems at the same time. These systems work together to flood the target with traffic until it can no longer respond to legitimate users.
The “distributed” nature of the attack makes it difficult to block, as the traffic appears to come from many different locations rather than a single attacker.
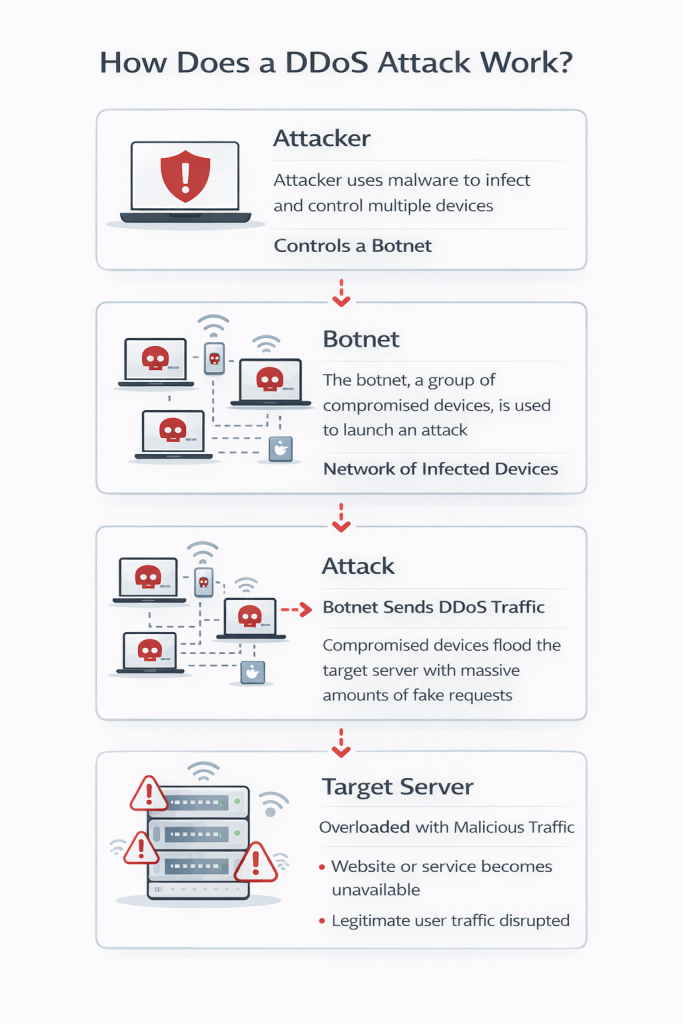
Most DDoS attacks rely on a network of compromised devices known as a botnet. These devices may include computers, servers, routers, or internet-connected devices that have been infected with malicious software.
The typical attack process includes:
Because each device sends a small amount of traffic, the attack can be hard to detect in its early stages.
DDoS attacks can take different forms depending on the attacker’s goal and the weakness being targeted.
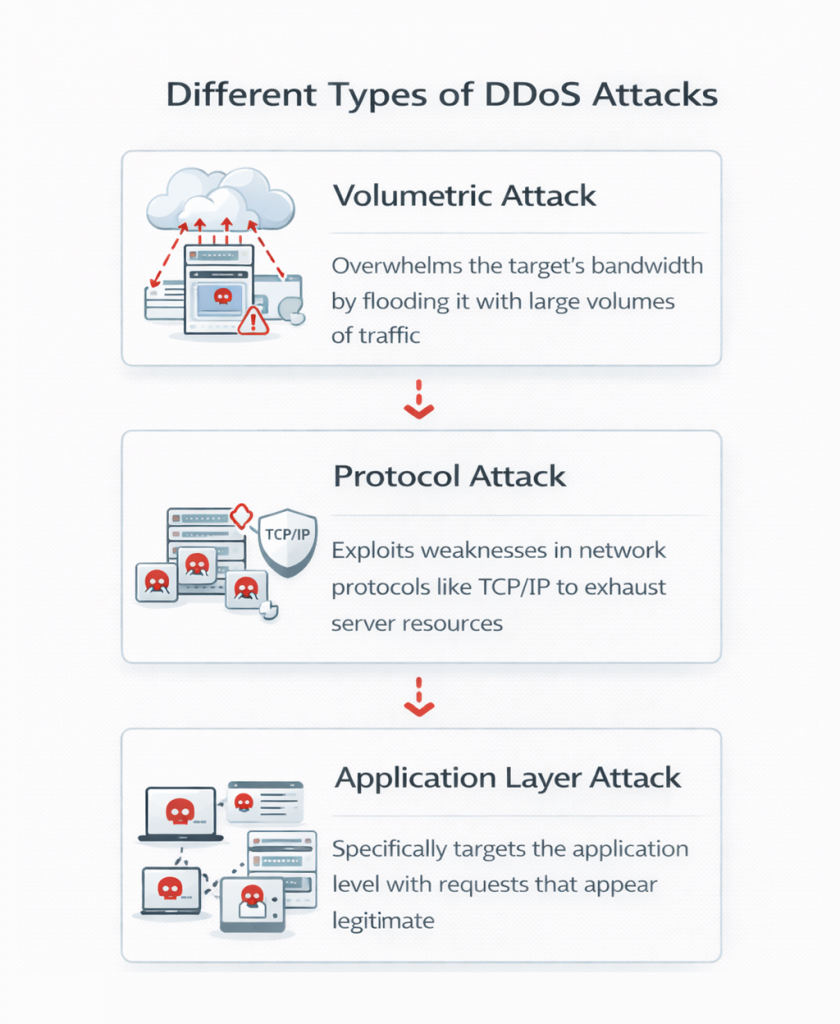
These attacks aim to consume all available bandwidth by sending massive amounts of traffic. The target becomes unreachable simply because the network capacity is exhausted.
Protocol attacks exploit weaknesses in how network connections are established and maintained. By sending incomplete or malformed requests, attackers force servers to waste resources handling fake connections.
These attacks target specific applications such as websites or APIs. They mimic normal user behavior, making them difficult to detect, while slowly exhausting server resources.
In more advanced scenarios, attackers combine multiple techniques at once. This makes mitigation more complex and increases the likelihood of prolonged downtime.
DDoS attacks are not just technical issues—they have real business consequences.
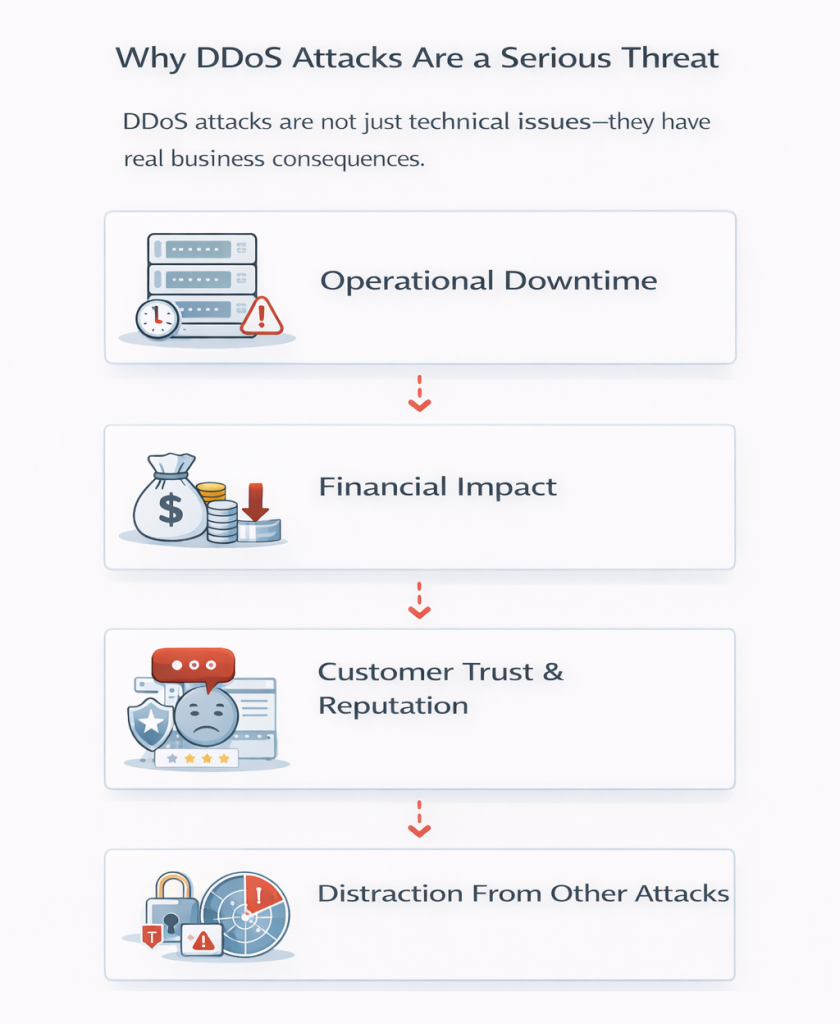
When services go offline, employees, customers, and partners are unable to access critical systems. Even a short outage can disrupt workflows and service delivery.
Lost revenue, recovery costs, and emergency mitigation efforts can quickly add up. For online-dependent businesses, downtime directly translates to financial loss.
Repeated service interruptions damage credibility. Users expect reliability, and prolonged outages can push customers toward competitors.
In some cases, DDoS attacks are used as a diversion while attackers attempt data breaches or system infiltration elsewhere.
Modern DDoS attacks are larger, faster, and more sophisticated than ever before. Attackers increasingly use automated tools and poorly secured internet-connected devices to amplify their attacks. Even small organizations are now being targeted, not just large enterprises.
The rise of cloud services and high-speed networks means attackers can generate enormous traffic volumes in seconds, leaving little time to react without proper defenses in place.
While it is impossible to eliminate the risk entirely, organizations can significantly reduce their exposure with the right approach.
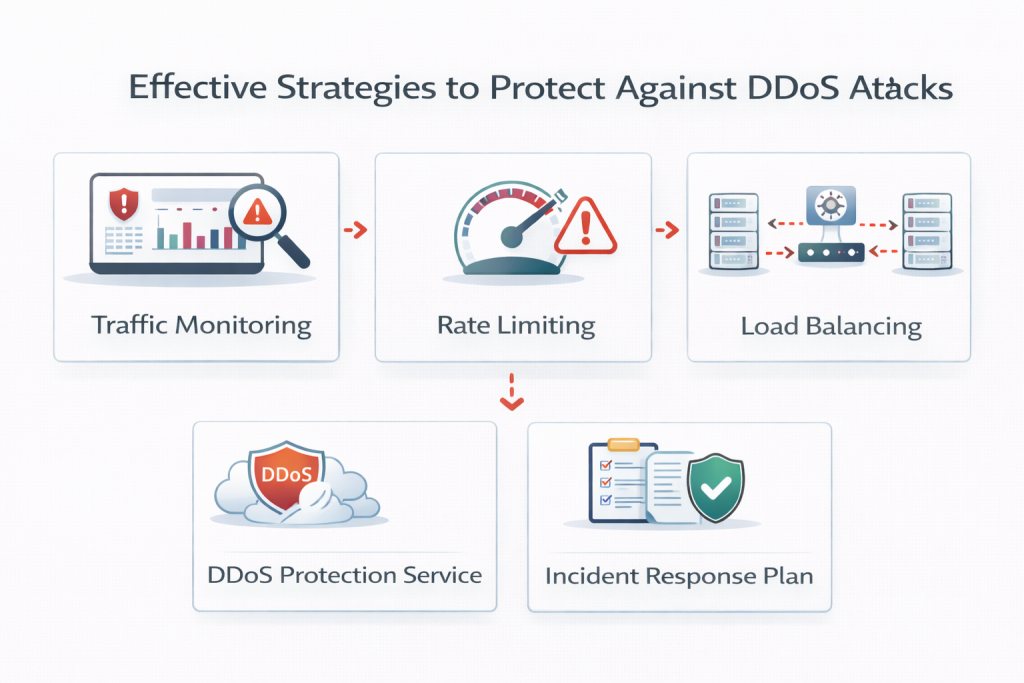
Monitoring normal traffic patterns helps identify sudden spikes or unusual behavior before systems fail.
Filtering malicious requests and limiting the number of requests per user reduces the impact of traffic floods.
Distributing workloads across multiple servers ensures that no single system becomes a point of failure.
Having predefined response procedures ensures faster recovery and minimizes confusion during an attack.
Regular testing, system updates, and security reviews also play a critical role in maintaining resilience.
DDoS attacks are designed to overwhelm, disrupt, and damage trust in digital services. As these attacks grow in scale and complexity, businesses must move beyond reactive responses and adopt proactive defense strategies.
Jaze ISP Manager helps ISPs stay resilient against DDoS threats by offering deep network visibility and real-time traffic insights through IPFIX logging in real-time. Based on these logs ISPs can identify attacks and trigger RTBH or BGP Flowspec records to mitigate the attack. This proactive approach ensures uninterrupted service delivery and stronger network reliability.